China's new data security regulation dropped provisions allowing government to access data from tech companies.
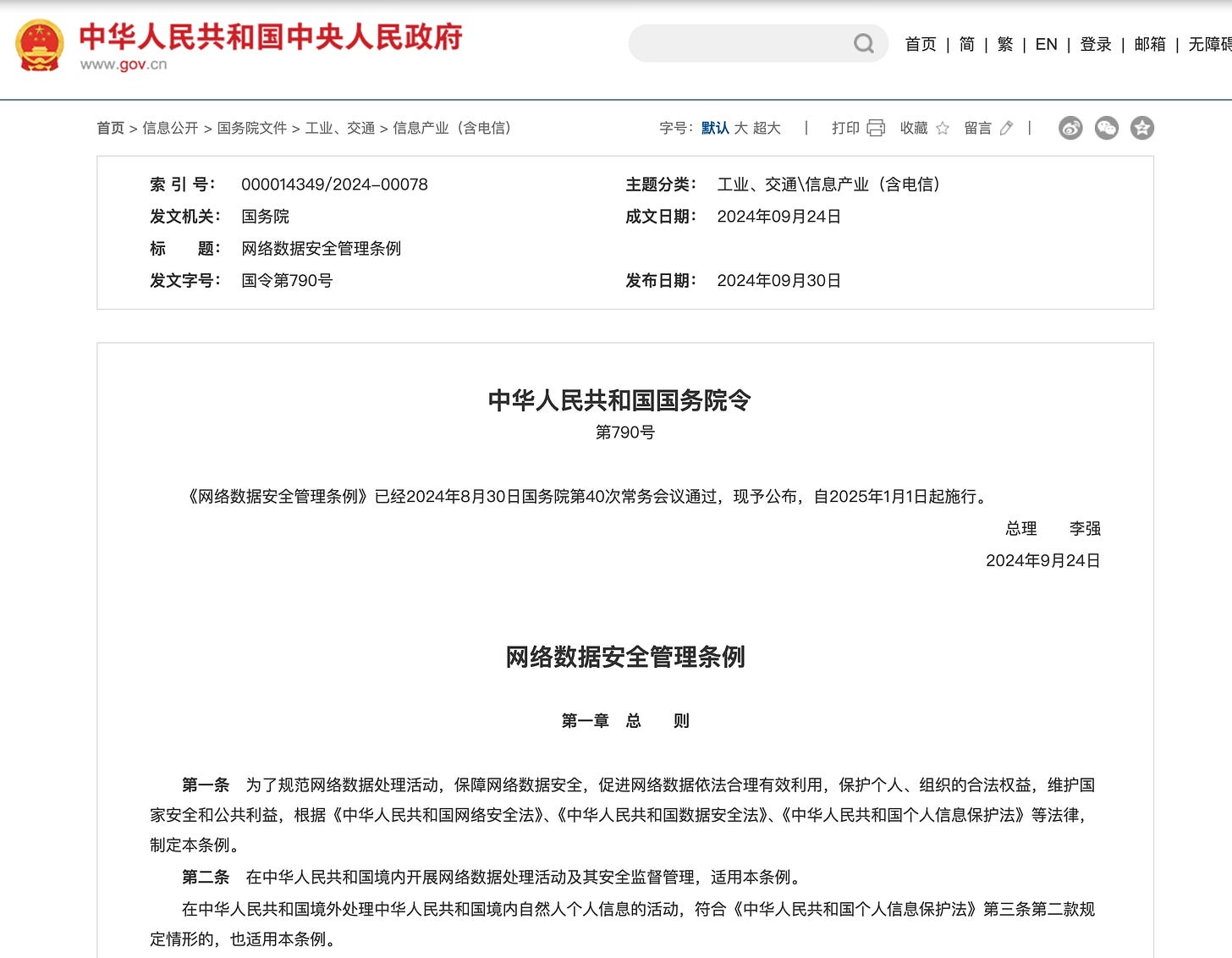
After approximately three years, China's most significant administrative regulation in the field of data security, the "Regulations on the Administration of Network Data Security" (网络数据安全管理条例, hereinafter referred to as the "Regulations"), has finally been promulgated.
China's legal system is structured into multiple levels, each with different legal force and scope of application. Generally, from highest to lowest, the hierarchy is as follows: Constitution(宪法), Laws(法律), Administrative Regulations(行政法规), Local Regulations(地方性法规), Departmental Rules(部门规章), and Local Rules(地方规章).
Administrative Regulations are legal documents formulated by the State Council based on the Constitution and laws. Their legal force is subordinate to laws but superior to local regulations and rules. The State Council, being China's highest administrative body, holds the authority to enact administrative regulations. These regulations primarily execute specific provisions of laws, clarify governmental management functions and responsibilities in various fields, and cover a wide range of content, including economic management, social management, environmental protection, public safety, and more. They are binding on governments at all levels nationwide, organizations, and citizens.
In 2021, the Data Security Law and the Personal Information Protection Law were passed. These two laws, enacted by the National People's Congress, laid the foundational provisions for data security protection in China. To provide more practical guidance, the State Council initiated the formulation of an administrative regulation themed on data security. Since the specific responsible department is the Cyberspace Administration of China (CAC), and the CAC's scope of duties only encompasses data existing in digital form (excluding other substantial amounts of offline data stored in paper texts, historical archives, etc.), the regulation limits its jurisdiction to "network data."(网络数据)
On November 14, 2021, the CAC officially released a draft of the "Regulations on the Administration of Network Data Security" and solicited public opinion.
Given the important position of this administrative regulation in China's data security protection legal system, China's legal and technical communities engaged in extensive discussions around the "Regulations." Generally, it was widely believed that the current draft was still immature, especially as it imposed overly broad, vague, and strict legal obligations on the private sector.
Specifically, some viewpoints argued that certain provisions of the "Regulations" were inconsistent with higher-level laws, established a large number of administrative licenses, and were suspected of over-regulation, inhibiting innovation in the data industry, and not aligning with the policy tone of "streamlining administration and delegating power." Other experts pointed out that the "Regulations" imposed excessive restrictions on data export, were not conducive to cross-border data flow, significantly constrained Chinese tech companies from conducting global business, increased platform operating costs and compliance burden, and were unfavorable to the development of the platform economy.
A large number of opposing opinions piled up on the legislators' desks, forcing the CAC to advance the formulation of the regulations more comprehensively and prudently.
After completing the solicitation of opinions, the CAC submitted the "Regulations (Draft for Review)" to the State Council, and the related work entered the stage of legislative review(立法审查) of the Ministry of Justice.
The Ministry of Justice extensively solicited opinions from relevant central government agencies, local governments, companies, institutions, industry associations, and scholars, conducted field research in local areas, held multiple symposiums with companies and industry associations to hear opinions, and repeatedly studied and revised the draft in conjunction with the CAC, forming a new version of the "Regulations (Draft)." On August 30, 2024, the State Council executive meeting reviewed and approved the new version of the "Regulations (Draft)."
The final version of the "Regulations" will officially come into effect on January 1, 2025. In my view, it essentially reiterates the core systems of the "Cybersecurity Law," "Data Security Law," and "Personal Information Protection Law," without introducing much new content. However, there are a few points worth noting:
Government Access to Data
A significant change in the final version of the "Regulations" compared to the draft is the deletion of provisions stating that Chinese government agencies have the authority to request data from tech platforms.
Due to provisions in China's "National Intelligence Law" and "National Security Law" regarding government access to data, countries like the United States have questioned whether China would require private companies under its jurisdiction to provide data stored overseas. Although the U.S.'s Foreign Intelligence Surveillance Act (FISA), the CLOUD Act, and national security laws of many of its allies also have provisions allowing collecting data from the private sector, China's regulations are perceived as particularly dangerous and illegitimate, potentially leading to arbitrary access to foreign data by the Chinese government.
In the "Global Initiative on Data Security" released by the Chinese government in 2019, China explicitly promised that it would not require Chinese companies to hand over data collected abroad to the Chinese government, and other governments should not be allowed to do so either.
"Global Initiative on Data Security" Excerpts:
Countries should require enterprises to strictly abide by local laws and not require their domestic companies to store data obtained overseas within their borders.
Countries should respect other nations' sovereignty, jurisdiction, and the right to manage data security, and should not directly access data located in other countries' enterprises or individuals without the permission of their laws.
If cross-border access to data is needed for law enforcement purposes such as combating crimes, it should be resolved through judicial assistance channels or other relevant multilateral or bilateral agreements. Bilateral agreements on cross-border data access between countries should not infringe upon the judicial sovereignty and data security of third countries.
Article 52 of the draft "Regulations" initially explicitly stipulated that "relevant departments of the State Council" have the authority to request or access data held by tech platforms, but in the final version, this article has disappeared.
Article 52 of the Draft "Regulations":
When relevant departments of the State Council need to retrieve or access public data and public information held by internet platform operators in performing their statutory duties, they shall specify the scope, type, purpose, and basis of retrieval or access, strictly limit it to the scope of performing statutory duties, and shall not use the retrieved or accessed public data and public information for purposes beyond performing statutory duties.
Internet platform operators shall cooperate with relevant departments in retrieving or accessing public data and public information.
Internet ID (Digital Identity)
In July, China's Ministry of Public Security and the Cyberspace Administration jointly released a proposed regulation for public feedback, claiming it would enhance the protection of citizens’ personal data. However, the new rule immediately drew intense backlash, with some Chinese scholars arguing that the new rules would give law enforcement more power to monitor ordinary people for their online behavior and opinions. The regulation would require internet content providers and platforms to make users register with a new internet ID linked to their national ID, allowing authorities to identify individuals quickly and accurately. This has been criticized by the West as an effort to enhance censorship or establish an oppressive rule reminiscent of George Orwell's 1984.
In fact, this policy was already disclosed in the 2021 draft of the "Regulations," although it did not attract much attention at the time.
Article 50 of the Draft "Regulations":
Article 50: The state shall build public service infrastructure for network identity authentication and provide personal identity authentication public services under the principles of government guidance and voluntary participation of netizens.
Internet platform operators shall support and give priority to using the personal identity authentication services provided by the national network identity authentication public service infrastructure.
Compared with the draft, the final version of the "Regulations" downplays the role of tech platforms: the wording used in the draft was "shall support,"(应当支持) but the final version uses the term "encouraged to support."(鼓励支持)
Article 43 of the "Regulations":
Article 43: The state promotes the construction of public services for network identity authentication and promotes their application based on government guidance and user voluntariness.
Network platform service providers are encouraged to support users in registering and verifying real identity information using national network identity authentication public services.
Keep reading with a 7-day free trial
Subscribe to Geopolitechs to keep reading this post and get 7 days of free access to the full post archives.